Arpspoof or often known as Arppoisoning is attack method that used the ARP protocol to get traffic between workstations such as server and client. So, what is ARP? In a simple manner ARP is a protocol that convert IP Addresses to the physical addresses (MAC Addresses). This attack method works by sending the Arp request to the victim so the victim’s Arp cache believed that the attacker mac address is the address that is should request to. Once, the victim requested the attacker would work similarly to the router/gateway and pass the request like router do and get the access to the packet traffic between victim and server.
Tools and IP’s used in this demonstration:
Gateway/router’s IP : 192.168.1.1
Victim’s IP: 192.168.1.101
Arpspoof (dsniff distribution)
Step by step of Arpspoof
1.Enable Packet Forwarding
Enabling Packet Forwarding will allow the packet to travel from one network to another network.
To enable Packet Forwarding, first, type in the “echo 1 > /proc/sys/net/ipv4/ip_forward” command in the terminal.
- Arpspoof
Arpspoof is a tool that will allow to intercept the traffic between two communicating network.
to use Arpspoof user can type the command in two different Kali Linux tab:
arpspoof -t [gateway’s ip] [victim ip]
arpspoof -t [victim’s ip] [gateway’s ip]
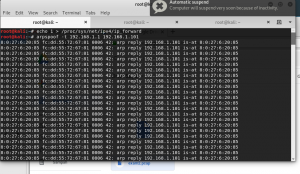
Img 1.1 arp spoof from victim to gateway
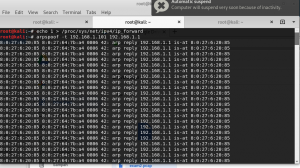
Img1.2arp spoof from gateway to victim
- Start packet Sniffer
In this demonstration TCPDump is the tool that is used for capturing the packet/data in the network traffic.
.pcap file can be created by typing the command:
tcpdump -vvn -i eth0 src [victim ip] -w [filename].pcap
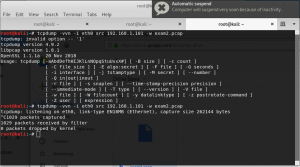
After the sniffing press on ctrl + C to stop the process and the .pcap file will be automatically created in the document directory.
- Use WireShark to do analysis on the pcap file
Similar to TcpDump, WireShark is a packet sniffing tool. However, unlike the TCPdump wireshark has user interface which make data analyzer easier to beginner.
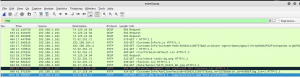
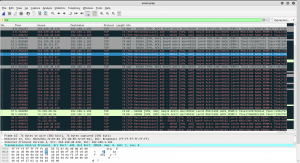
5.proof
Now the traffic of the victim is also recorded in the attacker sniffer.