Intelligent system week 7 progress
30 dec-6 Jan At the current week our project are near to it completion. however, some minor issues such as its inability to detect imagesize, converting the given image size […]

30 dec-6 Jan At the current week our project are near to it completion. however, some minor issues such as its inability to detect imagesize, converting the given image size […]
23 Dec-30Dec After prediction algorithm is tesed and built, the team started to do research for the comparison methodology. our team found out that there is several possible method to […]
17 Dec – 23 Dec The text recognition will be based on the tensorflow library. we also referenced from the code provided by niek algorithm in building the building the […]
9 dec – 16 dec After doing some research we found out that three neural network layer can be used to recognize handwritten letter.The CNN(convolutional neural network) layer, as the […]
1 Dec – 8 Dec After getting a code for reference our group run into some problems regarding the tensorflow installation. Some of the problems are we are unable to […]
24-31 October In the Second week, our group decided to use Python3 programming language as the base of the final project, as most of the existing framework in Python 3 […]
17 October – 23 October(1st Week) During this week our team focused on the idea of research. The idea research is expected to give a better overview of the current […]
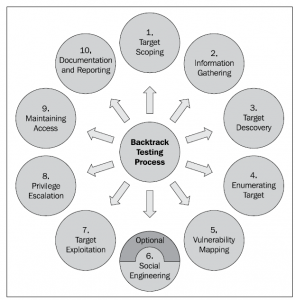
figure1.1 Kali Linux pentesting Cycle Target scoping Target scoping is the first step in kali Linux pentesting cycle, in this step we need to determine the action that we are […]
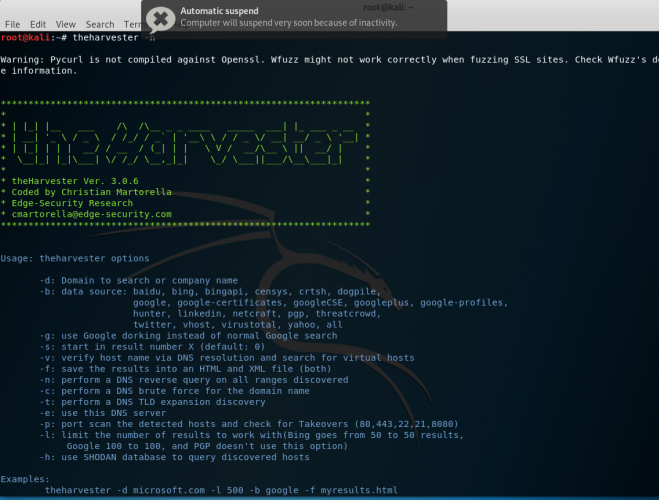
Theharvester is tools that are used to gather information related to emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines. To see the […]
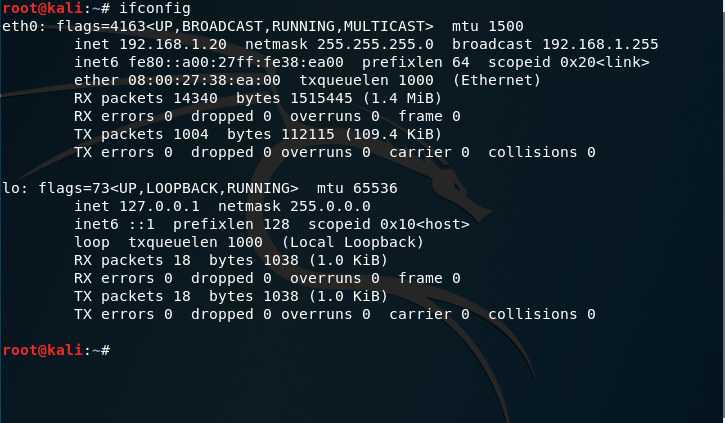
DNS spoofing is a form of network hacking, where the attacker alters the request to certain domain name to another ip address. This hacking technique is very effective to be […]