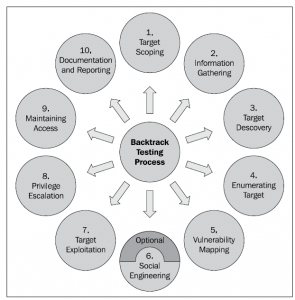
figure1.1 Kali Linux pentesting Cycle
Target scoping
Target scoping is the first step in kali Linux pentesting cycle, in this step we need to determine the action that we are going to take on the network, how long will the penetration testing will take, and the target of the pentesting.
Information Gathering
Gather and learn about the target from public sources like a search engine. it is also possible to get more detailed information through tools like whois.com and other footprinting tools.
Target discovery
in this step, we mostly deal with identifying target’s network status, OS, and network architecture.
Enumerating target
Target enumerating may include username enumerating, port enumerating and password enumerating.
Vulnerability mapping
The steps where the vulnerability assessment is created.
Social Engineering (optional)
Exploiting human errors to get useful information related to the target.
Target exploitation
In this step, real exploitation is done. This step focused on the target acquisition process that has three core area, includes :
pre-exploitation
exploitation
post-exploitation activities
privilege escalation
in this step usually, the attempt to get higher access to the system is done.
maintaining access
Keeping target under controls and Provides a clear view of how an attacker maintains access without noisy behavior.
documentation and reporting
Documenting, reporting, and presenting the vulnerabilities found.
