Intelligent system 1st week progress
17 October – 23 October(1st Week) During this week our team focused on the idea of research. The idea research is expected to give a better overview of the current […]

17 October – 23 October(1st Week) During this week our team focused on the idea of research. The idea research is expected to give a better overview of the current […]
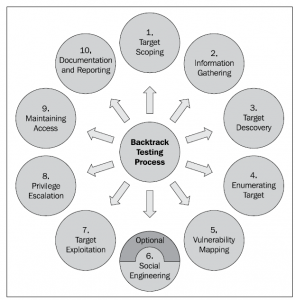
figure1.1 Kali Linux pentesting Cycle Target scoping Target scoping is the first step in kali Linux pentesting cycle, in this step we need to determine the action that we are […]
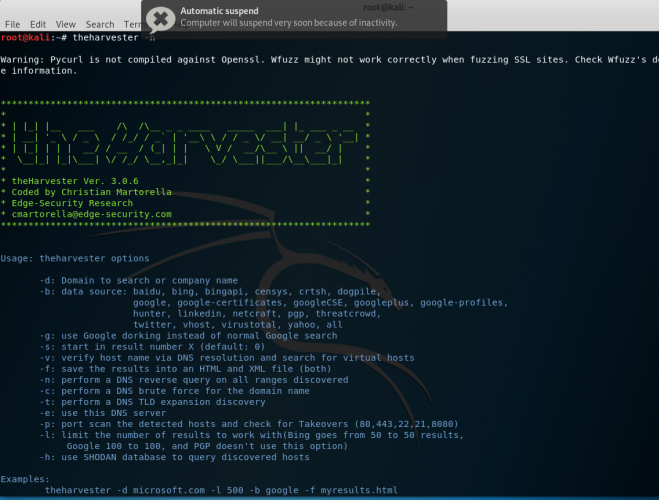
Theharvester is tools that are used to gather information related to emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines. To see the […]
DNS spoofing is a form of network hacking, where the attacker alters the request to certain domain name to another ip address. This hacking technique is very effective to be […]
Setoolkit is a frameworks focused mainly on social engineering. This tools consists of site duplicating tools, Java applet attacking tools and many other social engineering tools. In this post site […]
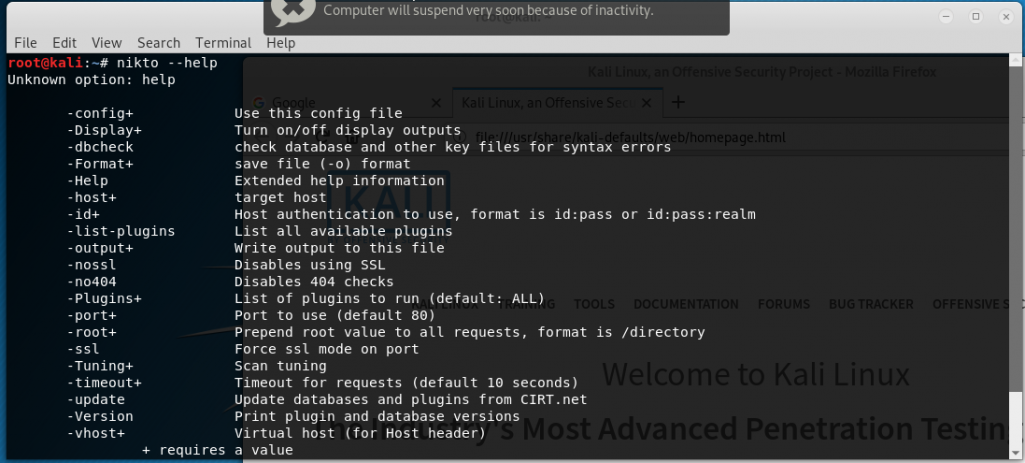
Nikto Scanner is a scanner that run through the kali linux terminal. By default Nikto is already is already installed on kali Linux. Nikto Is usually used for scanning vulnerabilities […]
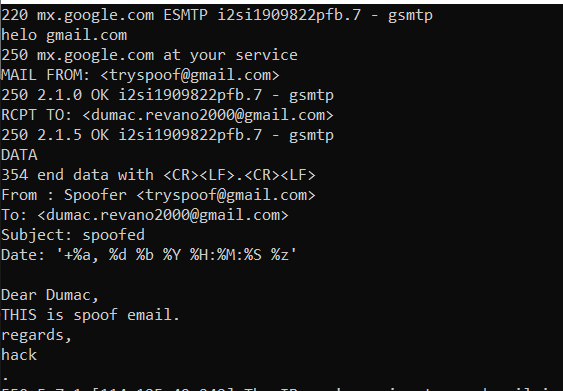
“All the posts posted in this blog are used for education purpose only” An SMTP server is a server that is in charge of delivering email. Hence, it is necessary, to configure […]
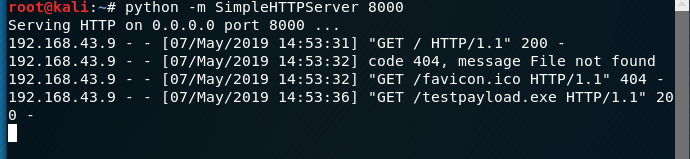
“Please Keep in mind that all the materials shared in this blog is mainly for education purpose” Taking over the system using the Trojan There is a lot of ways […]
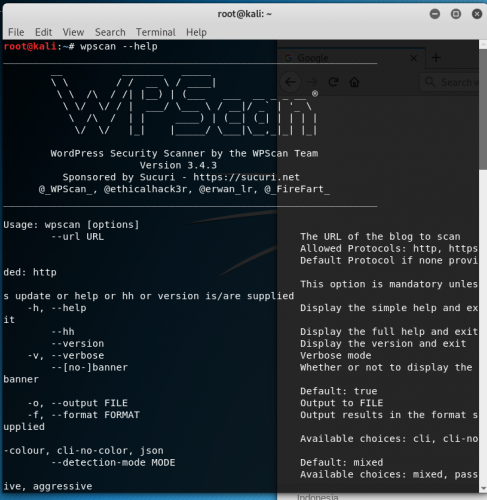
WP Scan is a tool that is mainly used for scanning vulnerabilities that can be found in any WordPress website. The type of vulnerabilities that can be scanned by Wpscan […]
Arpspoof or often known as Arppoisoning is attack method that used the ARP protocol to get traffic between workstations such as server and client. So, what is ARP? In a […]